If you watched the news in 2016 alone it would be pretty clear that many organizations are doing a very poor job in protecting the user credentials that are in their care. Even more, when organizations somehow lose credentials for hundreds of millions of users (looking at you Yahoo) and users are not fully up-in-arms about it we know we’re in a bad place – the place where users are so used to hearing bad news related to security or privacy that they almost don’t care anymore.
We can do better than this. The goal of this post is to present arguments on why authentication mechanisms in many organizations are failing and show why Identity as a Service (IDaaS) solutions such as Azure Active Directory B2C (business-to-consumer) are the future.
According to a Gartner report from June 2016 (see link below in the resources section) by 2020, 40% of identity and access management (IAM) purchases will use the identity and access management as a service (IDaaS) delivery model — up from less than 20% in 2016. If you’re planning to build any new consumer facing applications in the near future or if the security of your existing application credentials is keeping you up at night then you should seriously start to look at IDaaS solutions.
Challenges with traditional consumer identity and access management systems
Security & privacy risks
- The username/password list is a target for attackers – attackers look for easy targets knowing consumers often reuse login credentials across accounts (the credentials list is often more important than the data it protects)
- Developers often don’t really understand well how to properly secure passwords with custom solutions
- Attacks are getting more sophisticated / threats are constantly evolving
High TCO (total cost of ownership)
- Development time & costs – lots of code to write for identity management functions (sign-up/sign-in, email verification, password resets, MFA, user experience UI/UX)
- Software licensing, maintenance and upgrade costs (when using off-the-shelf software for identity management features)
- Identity management functionality is a moving target – for example in the Microsoft .NET world built-in identity management approaches change every 1-2 years (ASP.NET Membership, ASP.NET Identity) leaving behind fragmented applications that are hard to maintain
Scalability and availability challenges
- Consumer traffic is highly seasonal
- Organizations are forced to provision for peak capacity
- With millions of users this can be very costly
What is Identity as a Service (IDaaS) and where does it fit in?
- Cloud-based service that provides a set of identity and access management functions
- An authentication infrastructure that is built, hosted and managed by a third-party service provider
- This is in contrast to traditional identity and access management (IAM) solutions that are typically completely on-premises and delivered via bundled software and/or hardware means
- According to Gartner, IDaaS functionality includes:
- Identity governance and administration (“IGA”) — this includes the ability to provision identities held by the service to target applications
- Access — this includes user authentication, single sign-on (SSO), and authorization enforcement
- Intelligence — this includes logging events and providing reporting that can answer questions such as “who accessed what, and when?”
IDaaS sounds interesting … why consider Azure Active Directory B2C?
Yes – there are quite a few IDaaS solution providers out there – so why am I advocating for Azure AD B2C? To answer that I’ll just point to a recent June 2016 study (see link below) where Gartner analyzed the IDaaS space:

Microsoft with its IDaaS offerings is currently in the leader quadrant. The success of its IDaaS solution (Azure Active Directory) is very closely tied to the success and growth of Microsoft Azure – its cloud solution – and by all indications it has a strong future ahead of it.
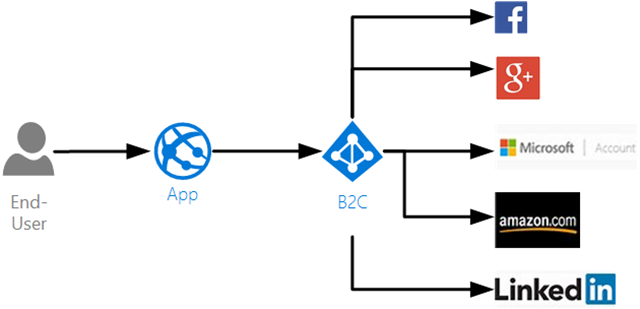
What exactly is Azure Active Directory B2C?
- Cloud identity service with support for social accounts and app-specific (local) accounts
- For enterprises and ISVs building consumer facing web, mobile & native apps
- Builds on Azure Active Directory – a global identity service serving hundreds of millions of users and billions of sign-ins per day (same directory system used by Microsoft online properties – Office 365, XBox Live and so on)
- Worldwide, highly-available, geo-redundant service – globally distributed directory across all of Microsoft Azure’s datacenters
How is it better than a custom authentication solution?
- Easy to integrate consumer self-service capabilities (sign-up, password resets)
- Site owner controls user experience (custom html & css for sign-in/sign-up)
- Enterprise-grade security with continuously evolving anomalous activity, anti-fraud and account compromise detection systems (offload security to the real domain experts)
- Benefits of security-at-scale – uses machine learning to watch billions of authentications per day across the entire Azure AD ecosystem and detect unusual behavior
- Superior economics compared to on-premises – pay-as-you-go pricing + free tier
- Based on open protocols and open standards – OAuth 2.0, OpenID Connect
- Uses open source libraries for .NET, Node.js, iOS, Android and others / REST-based Graph API for management
- Better and faster development experience for authentication / easy to integrate with existing sites wherever they’re running from (not just those in Azure)
- Ability to easily integrate social logins if needed (Facebook, Google and such)
- Support for MFA (multi-factor authentication)
- Authentication database is separate from the application data / easier to enable SSO (single sign on) later across other apps in the enterprise (unified view of the consumer across apps)
Sounds interesting – tell me more: who is using Azure AD B2C?
- Azure AD B2C is a natural choice for consumer facing apps hosted on Azure (but certainly not only for those)
- Some stats (from Microsoft presentations as recent as September 2016) on Microsoft Azure AD (the technology that B2C is built on)
- 90% of Fortune 500 companies use Microsoft Cloud
- More than 10 million Azure AD directories
- More than 750 million user accounts in Azure AD
- More than 110K third-party applications that use Azure AD each month
- More than 1.3 billion authentications every day with Azure AD
- The state of Indiana used Azure AD B2C for user authentication in order to integrate various features into a single citizen portal
- CASE STUDY! Creating a Citizen Identity for Indiana State with Azure B2C – if B2C can pass state regulations and requirements for security, availability and such that says something
- Real Madrid (one of the most popular soccer clubs on the planet) uses Azure AD B2C to offer authentication services for their mobile app used by more than 450 million fans (Microsoft case study)
What about security for all this authentication data in the cloud?
To answer the topic of security for authentication data when IDaaS solutions are used I’ll just include a quote from the Gartner report I mentioned above – I totally agree with their assessment:
No security is perfect. Ultimately, prospective customers must decide whether vendors’ stated control sets are sufficient for their needs. IDaaS vendors give significant attention to ensure the security of their platforms. Based on the number of enterprise security breaches that have been made public, and the lack of any such breaches for IDaaS providers, Gartner believes that IDaaS vendors are more likely to provide better security for IAM services than their customers could provide for themselves.
Additional Resources
- Modernize your app’s consumer identity management with Azure AD B2C – Azure AD B2C presentation from Microsoft Ignite 2016 (presentation slides)
- Gartner 2016 Magic Quadrant for Identity and Access Management as a Service
- 7 laws of identity whitepaper – a classic resource from Kim Cameron, Architect of Identity at Microsoft